SensePost CTM Tool
SensePost CTM Tool
About the SensePost CTM tool Methodology
SensePost is a leading independent provider of expert information security services. The SensePost Corporate threat modeling tool is designed for security experts users. The CTM Tool methodology consist of two key areas, entity and mappings.
Entity Overview:
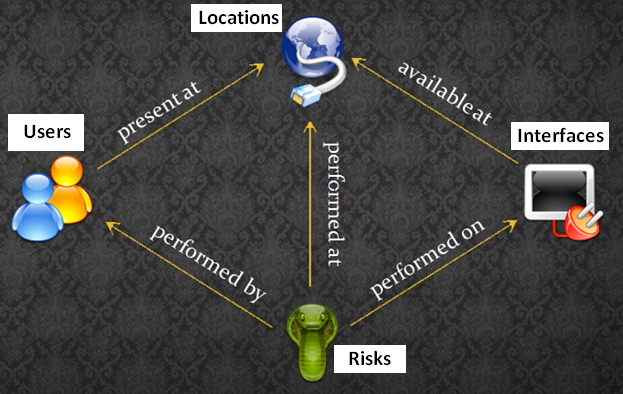
The CTM consist of four entities which are the locations, users, interfaces and threats. This tool uses these entities to map threats to users, location and interface.- Define - Trust of locations i.e. physical, logic and network locations
- Interfaces are exposed at locations
- Users are present at locations
- Trust of users i.e. External, internal or Anonymous users
- Users are mapped to locations
- Interfaces are exposed to users via locations
- Method of system access
- Asset Value
- Damage
- Likelihood
Mappings Overview:
Users to Locations:
Users are present at certain locations = Many to many mapping
Interface to Locations
Information was gathered from here